ARE THERE ANY GAPS IN YOUR UNDERSTANDING OF THE LATEST ATTACK VECTORS
THAT COULD POSE SIGNIFICANT RISKS TO YOUR CYBER SECURITY POSTURE?


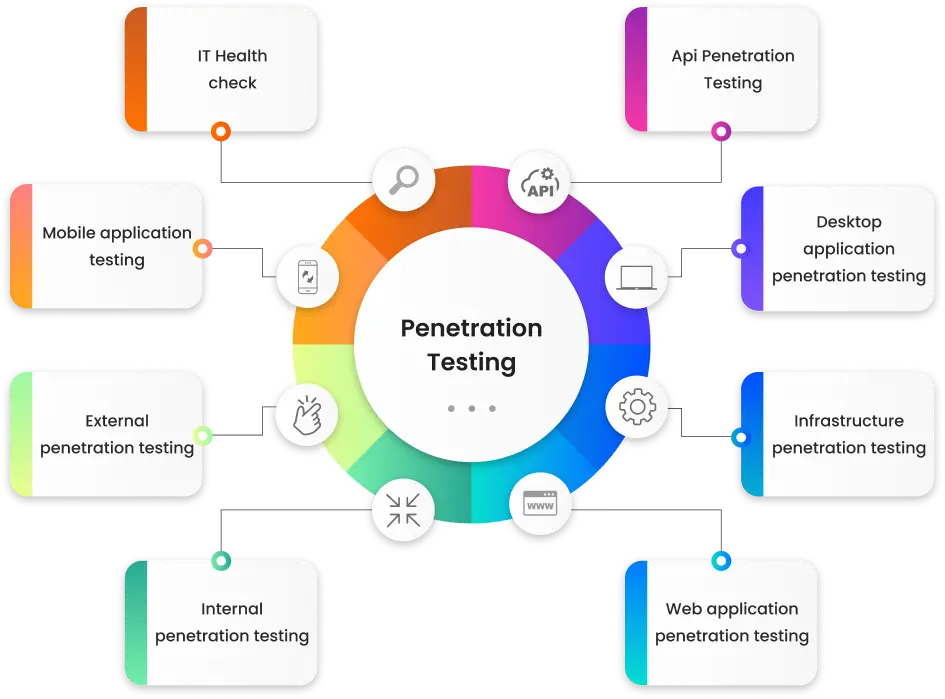
Penetration testing
Thorough testing to disclose security weaknesses of your systems: APIs, desktop apps, web infrastructure, and more. Identify vulnerabilities before the attackers do, with comprehensive assessments tailored to your environment.
Security Services
Analyze and harden your remote work setup with tests, phishing email checks, and dark web monitoring to protect your operations. Provide rock-solid network security: tests of VPN and firewalls, cyber maturity assessment, and more for holistic protection.

Remote working assessment

Phishing Email Assessment

Firewall ruleset review

Dark web monitoring

VPN Configuration Assessment

Network device security review

Cyber security maturity assessment
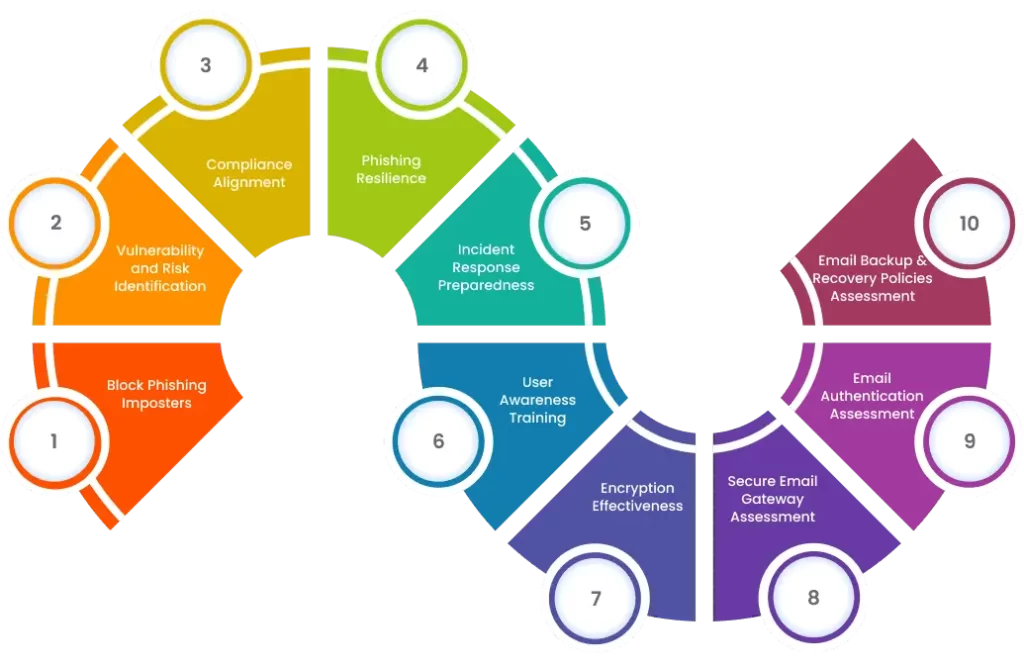
What Our Email Server Security Audit Delivers?
Defend against phishing and data breaches with an in-depth audit centered on phishing resilience, effectiveness in encryption, and incident response readiness. Be secure in your email infrastructure with tests regarding authentication, the effectiveness of gateways, and backup policies to maintain business continuity.

Why choose Technokraft?
- Go beyond vulnerability scanning : we don’t just stop at surface-level checks. We identify and successfully mitigate these vulnerabilities/ threats.
- Employee awareness training : We have training courses that teach employees about the best ways to protect themselves and their businesses online, which can help lower the chances of human mistakes being made.
- Remote Working Evaluation : As the number of employees working from home increases, we have become experts in evaluating the vulnerability of systems that are set up outside the office environment for organizations’ safety.
